App Analytics SDKs Could Expose Sensitive Data
The Symantec mobile team explains how popular mobile apps are using screen-recording SDKs to collect data on users – data that can be exposed in the absence of security measures
Your mobile screens are being recorded.
At a time when user experience can make or break a business, app developers are turning more and more to third-party app analytics tools to help them get insight on how customers interact with their apps. Glassbox, Appsee, TestFairy, and UXCam are a handful of popular analytics SDKs used by app developers to track in-app user behavior, crashes, bugs, and other issues that may impact the business. Many of these SDKs collect data by recording mobile device screens – at best, these recordings can be useful for understanding user behavior; at worst, they can be leaked, exposing sensitive data if information is not concealed properly.
This is what happened recently in several widely-used iPhone apps of hotels, airlines, cell phone carriers, banks, and others, using analytics SDKs to record their users’ screens. According to the TechCrunch blog post that first broke the story, popular travel apps used the Glassbox analytics SDK for “session replays” and screen-recording of user behavior, but failed to explicitly mention this in their privacy policies leaving their customers with no idea their actions were being captured. Since SDKs like Glassbox do not require app developers to mask sensitive data captured from screen recordings or to securely store and transfer session replay files, anyone who has access to the recording files can see the sensitive data.
In the aftermath of the TechCrunch report, Apple issued a warning to app developers, ordering them to remove the analytics code from their apps or properly inform users of the screen recordings. Failing to comply, Apple said, would result in the app being removed from the company’s App Store.
Sensitive Data Not Being Masked Properly
While gathering information such as crash date and time is harmless, SDKs can collect more personal data that violates certain privacy policies, especially when the data is not properly obfuscated. The Glassbox SDK can collect almost all data an app user enters into a screen, like passwords and credit card info, as well as mouse movements, clicks, scrolling, swiping, tapping, and more. Generally, the session replays of these activities are sent to the server of the analytics vendor or saved on the app developer’s server. When the data is not concealed properly, anyone who can access the screenshot database can see the information.
This incident is just another salient example of the risk posed to mobile users by apps believed to be secured but which, in fact, are vulnerable to data exposures.
Prevalence of Mobile Apps with Screen Recording Capabilities on Enterprise Devices
Research from Symantec Endpoint Protection Mobile (SEP Mobile), Symantec’s enterprise mobile threat defense solution, found that several other apps used by SEP Mobile customers employed the Glassbox SDK, including banking and credit card apps, putting a user’s financial information at risk of exposure.
We looked into hundreds of apps used by end-users in our enterprise installed base and found the following:
Number of affected Apps using GlassBox SDK:
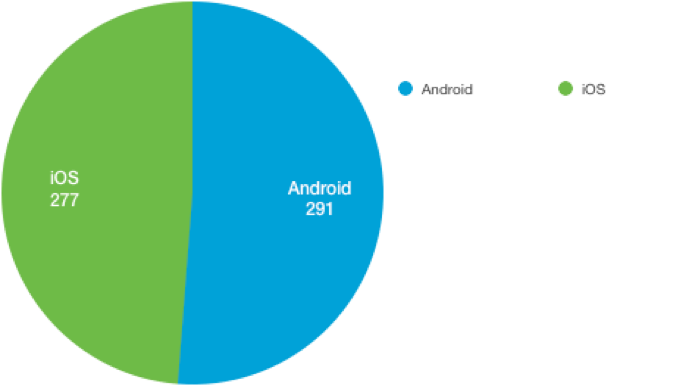
Number of affected Apps using UXCam SDK:
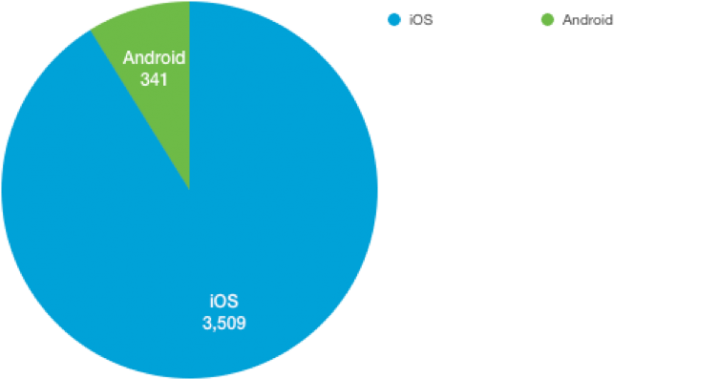
We also found that an app from a popular clothing retailer used another analytics SDK to send user/device information to Com Laude (an online brand protection service) over http:
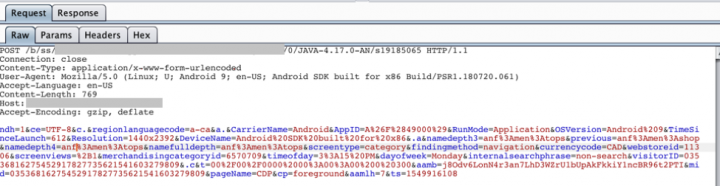
Attackers can exploit this type of information to geolocate users or profile their behavior, especially when combined with other information collected from a user’s Address Book, Camera, Apple Wallet, and other apps.
Previous research we conducted showed that the risks extend to enterprise. We found that apps with analytics SDKs that are used in enterprise mobile environments can increase the risk of sensitive corporate data being leaked to third-parties, without organizations being able to exercise any control over it. Our research showed that apps with the Appsee and TestFairy SDKs which also have screen-recording abilities, were able to open corporate documents such as Word, Excel and PDF files.
Getting Greater Visibility on Vulnerable Apps
The SEP Mobile research team continuously scans and analyzes apps used by our installed base for risky behaviors. In response to TechCrunch’s Glassbox report, our team analyzed all analytics SDK-using apps in our customer mobile environments and identified those that may be vulnerable to data exposures.
SEP Mobile customers can use our powerful app analysis engines to identify and protect against apps that may be vulnerable to data exposures, whether due to third-party analytics SDKs or other risky or unwanted behaviors. Apps that are found to be non-compliant with an organization’s mobile security policy can be flagged, allowing admins to take actions to mitigate the risk of corporate data leakage.

Platform Shift A LIVE Digital News Event
Join us for a digital news event to hear how Symantec and our partners are working together to drive down the cost and complexity of cyber security, while protecting enterprises against sophisticated threats.








We encourage you to share your thoughts on your favorite social platform.