Spyware Employs Various Obfuscation Techniques to Bypass Static Analysis
A look at some deceptive tactics used by malware authors in an effort to evade analysis.
With the surging popularity of mobile applications, the landscape of cybersecurity is encountering increasingly intricate and discreet forms of malicious software.
One common strategy in the realm of cybersecurity is code obfuscation. This practice involves the deliberate alteration of various elements within the code, such as variables, functions, and class names, rendering them virtually indecipherable. This not only poses a formidable challenge for anyone attempting to discern their purpose from their names but also significantly amplifies the complexity involved in decompilation.
Recently, our attention was caught by a Spyware cluster, which has employed a series of ingenious techniques to heighten the difficulties associated with static analysis. These methods, which we will discuss below, draw inspiration from diverse sources, some originating from resilient services and others from various "tools" at the disposal of these unscrupulous actors.
Analysis of Deceptive Tactics
Resource Camouflage
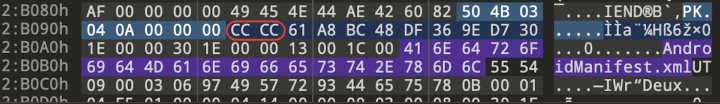
The world of mobile application security is rife with inventive techniques for concealing essential resources within APK files, the containers that hold Android applications. One such strategy involves creating directories within the APK that share the same names and permissions as vital resources. Figure 1 provides a visual representation of this approach.
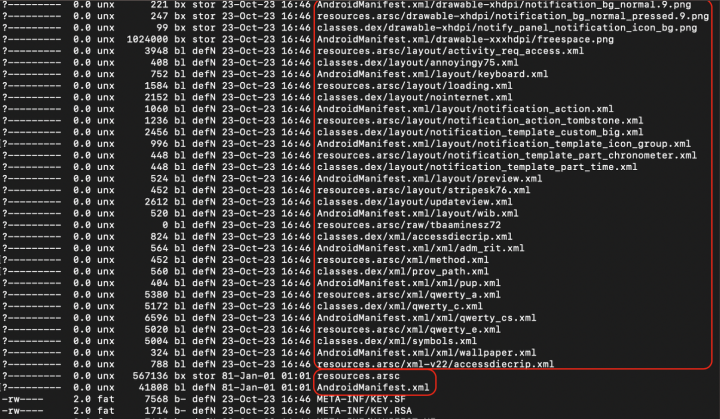
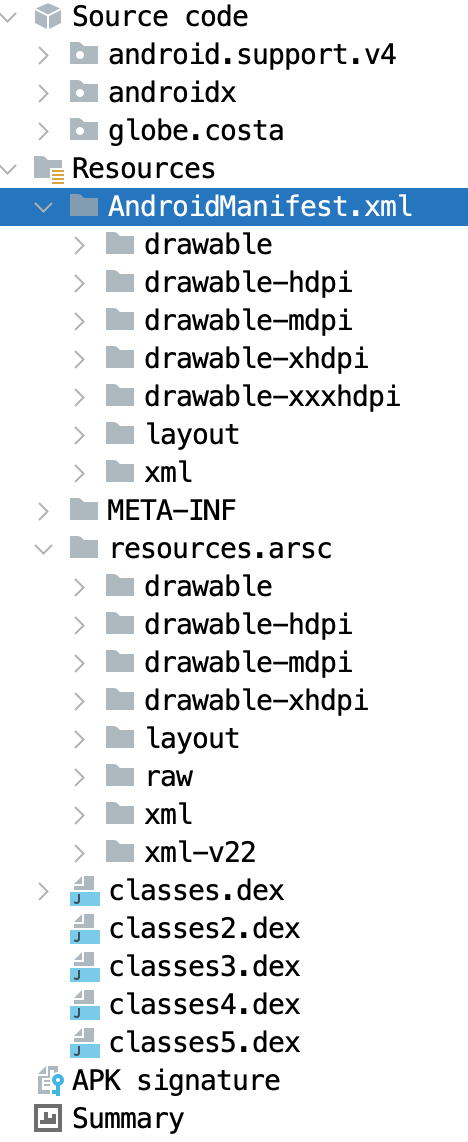
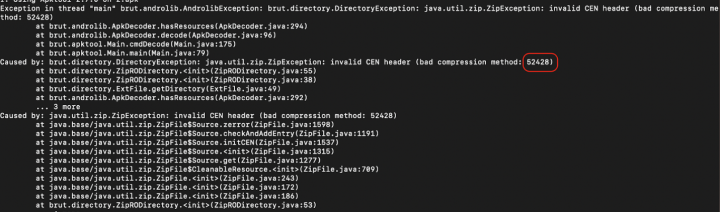
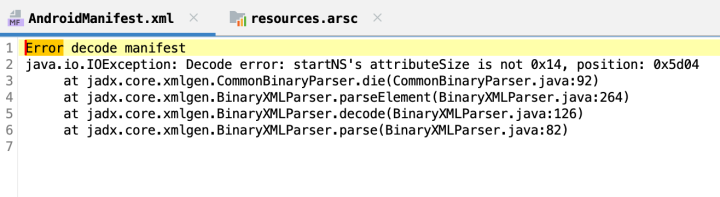
This technique presents complications for various analysis tools. For instance, Jadx, a popular decompiler for Android applications, can encounter problems when attempting to extract the AndroidManifest.xml file from these disguised directories. Figure 2 shows the wrong extraction in Jadx.
Compression Trickery
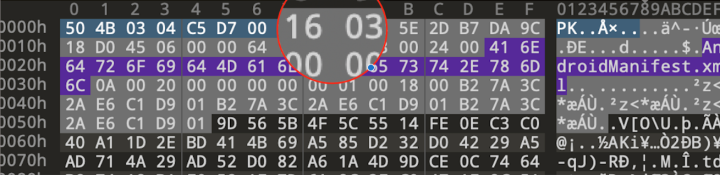
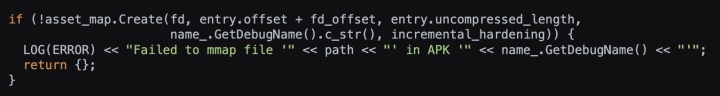
Another sneaky method involves hiding critical resources within an APK using an unsupported compression method for the local file header, while employing the correct compression method in the central directory file header. Figure 3 is the snapshot of deceptive compression code. This deceptive maneuver also leads to issues with certain tools, including third-party libraries, causing them to malfunction. Figure 4 shows the error messages printed from the tools.
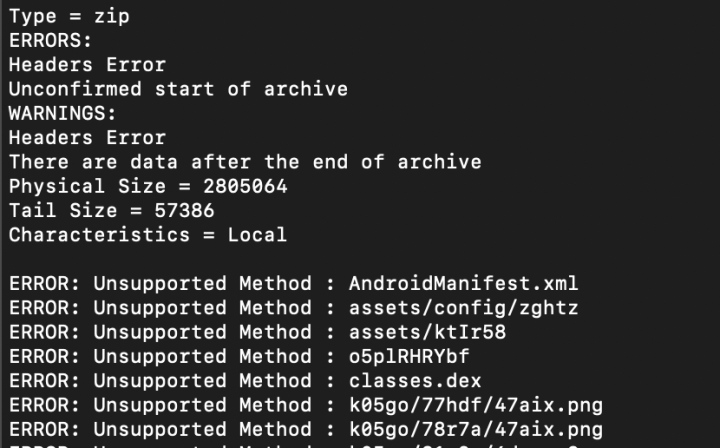
Nonetheless, Android can manage this effectively because it can retrieve the “correct” compression method from the central directory file header.
Signature Scheme Evasion through 'No Compression' Data"
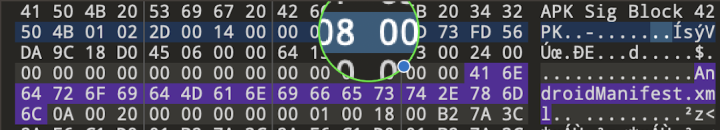
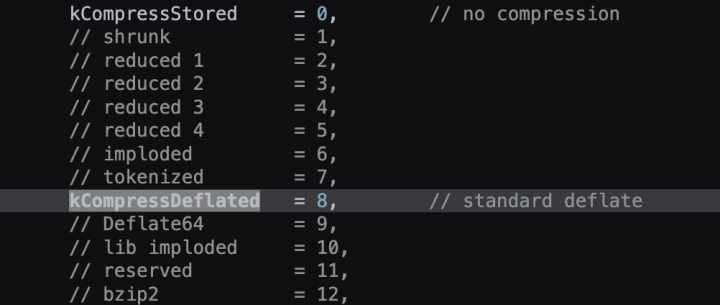
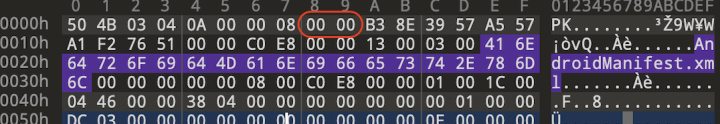
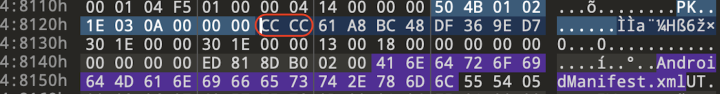
Exploring further within these covert techniques, we encounter the intriguing utilization of "no compression" data. Android currently supports both the no compression mode and the standard deflate compression mode (as shown in Figure 6). Traditionally, in Android's mapping, the no compression entry is represented as zero and begins with “00 00” (as seen in Figure 7). However, what piqued our interest is the presence of obfuscated entry codes within this spyware cluster (as displayed in Figures 8 and 9). Despite these unique entry codes, these spyware variants can still be installed on Android devices.
Android's support for both the no compression and standard deflate compression methods is pivotal in managing these scenarios. For higher Android versions that employ APK signature schemes V2 and V3, the system adeptly handles "no compression" even when faced with unsupported compression entry codes in both file headers. This seamless handling ensures the smooth installation of APKs, despite the presence of obfuscated entry codes (as evident in Figure 10).
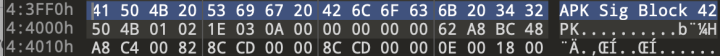
Then this group of spywares makes use of the design, and specifies them to support APK signature schemes V2 and V3 only (Figure 11, 12). We can see the V2 and V3 signatures schemes as well as the APK signature block number for V2+ (Figure 13).
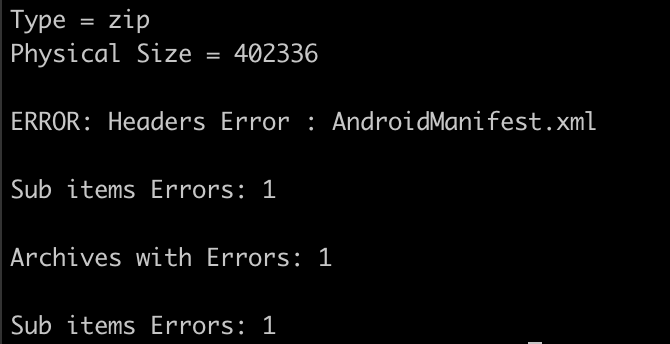
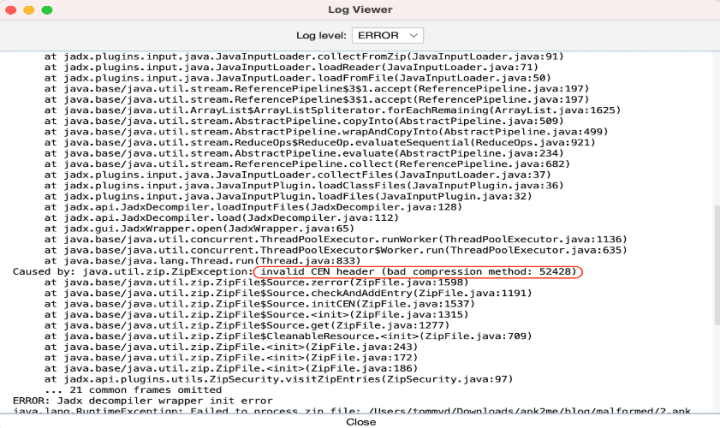
By doing so, these spywares effectively shield themselves from static analysis by various commonly used tools. For example, Apktool may falter in decoding due to the usage of a non-standard compression method (Figure 14). Zipping libraries like Unzip and 7z may struggle to extract files, as they strictly adhere to the legal ZIP format (Figure 15). Jadx may also face challenges when dealing with files manipulated in this manner (Figure 16).
Resource Obfuscation
“Obfuscated” AndroidManifest.xml and resources.arsc files can disrupt reverse engineering tools. With invalid attributes and illegal resource IDs, for example, the Android system doesn't parse illegal resource ID numbers, so while adding such a redundant attribute may not affect the APK's regular functionality, it can still cause issues with reverse engineering tools like Apktool, Jadx, JEB, etc. (Figure 17).
Analysis of App Behaviors
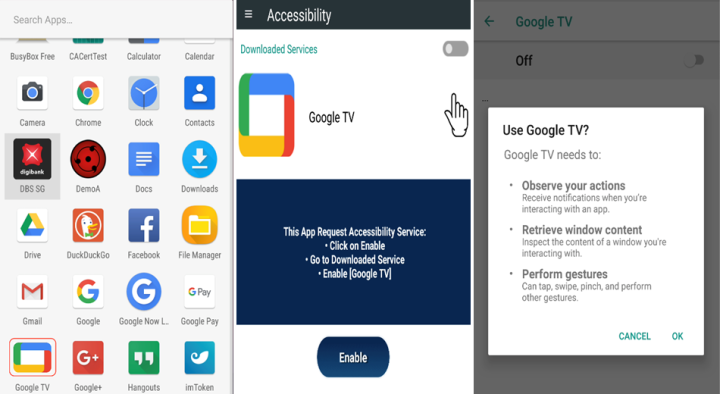
The spyware cluster, along with its variants, goes to great lengths to conceal its true identity by masquerading as well-known games, popular apps, and even system-level applications. Among the list of decoys are prominent names like Play Store, Google TV, Google Meet, Google Translate, Chrome, YouTube, Netflix, TikTok, Discord, Spotify, Angry Birds, Facebook Lite, Instagram, , Disney+, Snapchat, and Android Settings. To further enhance their deception, they engage in app repackaging, essentially dressing themselves up as these widely recognized apps to appear even more convincing to unsuspecting users.

When an unsuspecting user installs and opens one of these misleading applications, it will persistently seek accessibility permissions (as depicted in Figure 19). While this may appear innocuous, it is merely the beginning of a more complex operation. Through interactions with the user interface, these apps discreetly secure sensitive permissions and disable power optimization, as demonstrated in GIF 1.

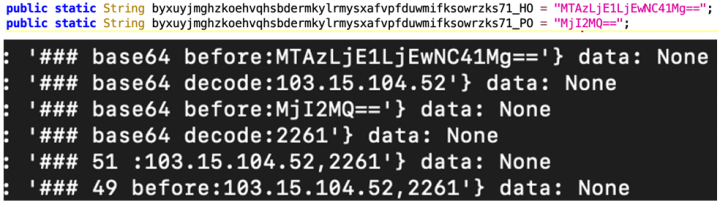
Although the default servers are not valid so far. To gather additional data and simulate the responses necessary to trigger malicious behaviors, we set up a mock server. The deceptive apps send fundamental app data, system information, and configuration details to this server and await further instructions (Figure 21).
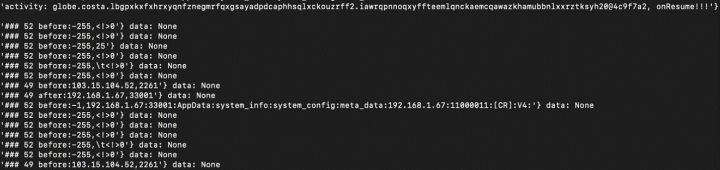
Moreover, once granted accessibility access, these apps can monitor and report a user's application activities to a designated server (Figure 22). All this activity is transmitted to the server after being encrypted (Figure 23).
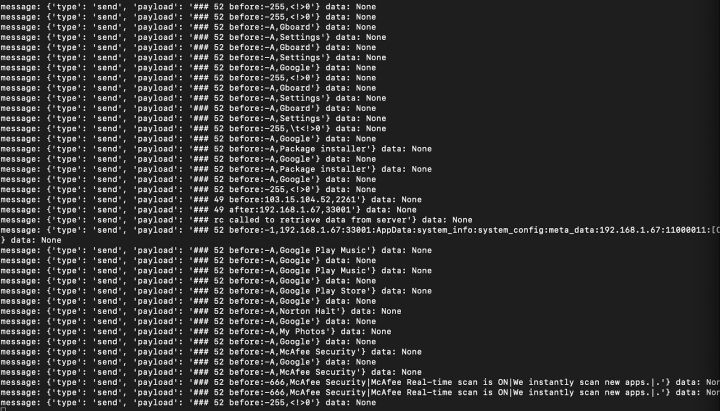
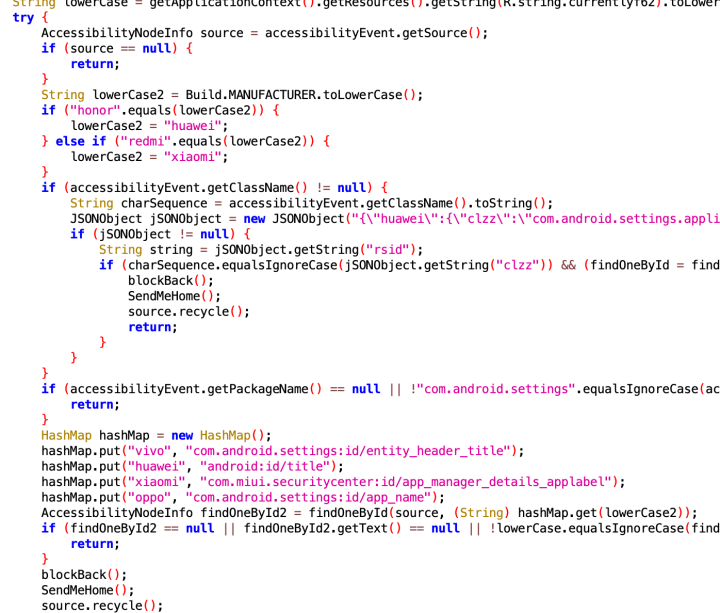
Let's delve into the intricacies of the C&C sections. These sections intentionally introduce noise, including junk code and irrelevant strings, into essential methods such as communication and command parsing (Figure 24). Their aim is to disrupt the functioning of static analysis tools like Jadx.
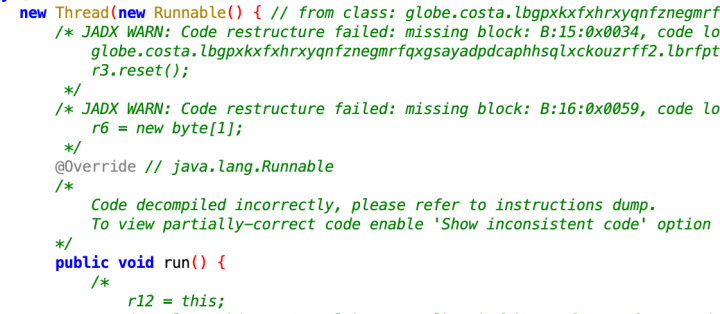
By stripping away this noise, we can discern that the server's response adheres to a specific format (Figure 25). The length components have variable lengths and end with '0', while the data content incorporates commands with GZIP compression.

The command handler AsyncTask is awaiting valid commands to be delivered from the server after launching the application (Figure 26).
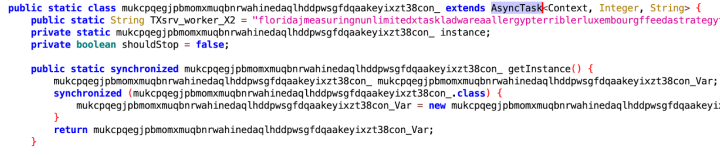
Once we remove the noise from the command parser code, it becomes evident that it possesses substantial capabilities. We listed a few of them in Table 1.
| Feature | Command |
|---|---|
| Toast alert | [data][Separator]msg:[data][Separator][data][Separator][data][Separator]ddll[Separator]... |
| Google Authenticator app | [data][Separator]goauth... |
| Media record | [data][Separator]srecon/off... |
| Upload record | [data][Separator]GRC... |
| Enable run in background | [data][Separator]rmiuibg... |
| Upload selected record | [data][Separator]gtrc[name]#[name]... |
| Collect Camera Info | [data][Separator]lcm... |
| Open URL | [data][Separator]lnkSTP/mon[URL]... |
| Send SMS | (all contacts/specified number) [data][Separator]ssmsall/[Dest]#[Text]... |
| Disable Apps | (via auto-click HOME and BACK) [data][Separator]CRDE>/D>[Package name]... |
| Device Admin | (lock device or wipe data) [data][Separator]admlck/wip... |
| Auto-Click | [data][Separator]Aclk{X,Y}... |
| Request Senstive Permissions | (Auto granted by UI operation via Accessiblity) [data][Separator]RPM[lod]... |
| Upload Screen Text | [data][Separator]SCRD... |
| Upload Logs | [data][Separator]srdall... |
| Gesture Click/Hold | [data][Separator]spclk/Bc... |
| Keep Device Awake | [data][Separator]spHo... |
| Take Screenshot | [data][Separator]spSK... |
| Enable Observer for uploading Screenshot | [data][Separator]spSK2... |
| Unlock PIN | [data][Separator]spUPIN... |
| Dynamic Load Dex | ... |
| Show Window View | ... |
| ... | ... |
To verify our findings, we employed a toast alert and sendSMS command for testing purposes. The commands delivered by our mock server were executed successfully (Figure 27).
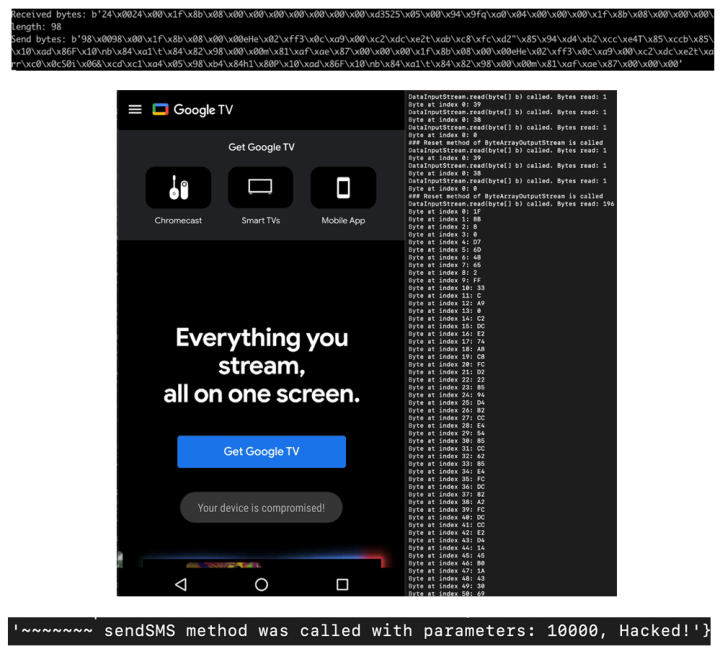
The spywares also have anti-killing/uninstalling methods to protect themselves. When the app detects that the user is trying to kill or uninstall itself through accessibility, it triggers the 'HOME' or 'BACK' action (Figure 28).
Conclusion
In the realm of mobile application security, we've explored a range of deceptive tactics, including resource camouflage, compression trickery, signature scheme evasion, and resource obfuscation. These techniques pose challenges for users and defenders, making it crucial for security experts to understand these tactics to counter evolving threats effectively.
Users who have installed Broadcom SEP Mobile will be shielded from this particular set of spyware threats.
Protection/Mitigation
For the latest protection updates, please visit the Symantec Protection Bulletin.
Symantec recommends users follow these best practices to stay protected from mobile threats:
- Install a suitable security app, such as Symantec Endpoint Protection, to protect your device and data
- Refrain from downloading apps from unfamiliar sites and only install apps from trusted sources
- Keep your software up to date
- Pay close attention to the permissions that apps request
- Make frequent backups of important data








We encourage you to share your thoughts on your favorite social platform.