Disrupting the Attack Chain Through Detecting Credential Dumping
Credential dumping is an essential step in the attack chain. Symantec’s defense-in-depth portfolio detects and blocks credential dumping and associated attack events.
There are various steps that an attacker must follow in order to execute any successful attack, with the initial compromise being just one stage in the overall attack chain. Once attackers have successfully breached the perimeter of an organization, they enter into the lateral movement phase where they attempt to tiptoe through a network, identifying the systems and data that are the ultimate target of their campaign.
Credential dumping is a technique frequently used by attackers during lateral movement to obtain account information, such as logins and passwords. Armed with this information, the attackers can then spread further within an organization and/or access restricted data. Attackers use a variety of different credential-dumping methods that require first obtaining administrator privileges. This process is known as privilege escalation and it must be performed before any attempts at credential dumping.
Detecting and blocking lateral movement activity is an important part of any organization's defense strategy and our Symantec portfolio provides defense-in-depth across control points. Our solutions detect and prevent credential dumping, and also protect against precursor events such as threat delivery and privilege escalation, as well as post-theft credential use.
Detecting methods of credential dumping
Credential dumping has long been used as a step in post-breach lateral movement and is listed as T1003 in the MITRE ATT&CK™ Framework. One of the challenges in protecting against all forms of credential dumping is that attackers attempt to masquerade their methods as legitimate activity, sometimes leveraging standard administrative tools to achieve the dumping. There are also easily available tools online, such as Hacktool.Mimikatz, which use a variety of methods to dump credentials.
Attempts at credential dumping can be uncovered in a variety of ways by our Symantec solutions. Here, I will discuss how our Symantec Endpoint Detection and Response (SEDR) product provides visibility into attempted credential theft by identifying a wide range of credential-dumping techniques, including:
- Access to the Security Accounts Manager (SAM) area of the registry
- Keylogging
- Sniffing credentials from network traffic
- Reading protected storage on the system
- Accessing memory of user applications where user credentials are stored (e.g. mail clients, internet browsers)
- Accessing credentials in the Windows Credential Manager
- Abusing Kerberos Ticket-Granting Services to harvest ticket hashes for offline cracking of credentials
- Injecting into Windows' Local Security Authority Subsystem Service (LSASS)
- Reading LSASS memory
When any suspected credential theft is found, regardless of the specific tool used to access the credentials, SEDR reports exactly what was observed along with the relevant MITRE ATT&CK tactic (the attacker's goal) and technique (how the attacker was trying to achieve that goal):
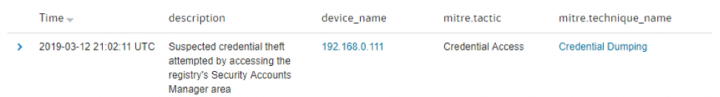
Symantec EDR will automatically pull in related activity to the credential dumping detection, in order to provide more context around the breach. SEDR leverages our Targeted Attack Analytics (TAA) technology, which combines the capabilities of our world-leading security experts with advanced artificial intelligence and machine learning to provide organizations with their own "virtual analysts". TAA correlates local events within an organization with information from Symantec’s massive global security telemetry data store to build out the full picture of attacker movement in the organization. Since its inception, TAA has detected security incidents at thousands of organizations, automating what would have taken many hours of analyst time. Examples of additional events that TAA can correlate to attempted credential dumping include:
- Suspicious deployment of executable files, such as remote access tools or password harvesting tools across an enterprise through network shares or removable media
- Suspicious remote execution of multi-purpose tools such as PSExec, Powershell, and Windows Management Instrumentation clients in an enterprise
- Suspicious activity around Windows Administrative Shares
- Suspicious activity around Windows Remote Management
- Exploitation of remote services within the customer network
- Subverting logon scripts to establish persistence on endpoints
In addition to the detection provided by SEDR, Symantec Endpoint Protection (SEP) uses a variety of technologies to block credential-dumping techniques, including:
- Behavior analysis – performs real time analysis of all running processes
- Reputation – correlates information about a program across telemetry from millions of Symantec customers
- Emulation – performs pre-execution evaluation of the process's activity
- Heuristics – looks for known suspicious attributes of a program that are associated with credential dumping
- Machine Learning – uses techniques that mimic the human brain to identify malicious processes
Alerts from these technologies are displayed in SEP as:
- SONAR.DumpSAM!gen2
- SONAR.PWDumpX!gen1
- SONAR.SuspInject!gen3
- Pwdump
- Hacktool.PasswdDumper
- SONAR.Mimikatz!gen3
- SONAR.Mimikatz!gen8
- SONAR.Mimikatz!gen9
- SONAR.Mimikatz!gen12
- SONAR.Mimikatz!gen13
- Hacktool.Mimikatz
- Hacktool.Credix
- SONAR.Powershell
Symantec Endpoint Protection and Symantec Endpoint Detection and Response are just two offerings across Symantec's defense-in-depth portfolio that can help identify and block credential theft at various points in the attack chain.
Our threat research teams continue to identify new credential dumping techniques being used in both targeted attacks as well as cyber crime activity. We look forward to sharing more both about the evolution of these attacks and about how Symantec's broad portfolio protects our customers against them.









We encourage you to share your thoughts on your favorite social platform.