Is Data Security A Priority for Your Workplace Equity Provider?
Trusaic
JULY 25, 2023
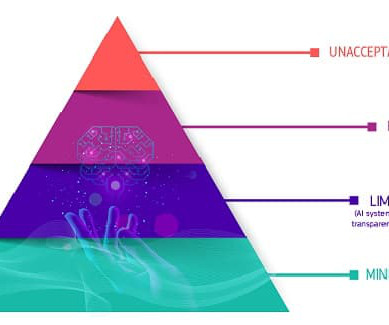
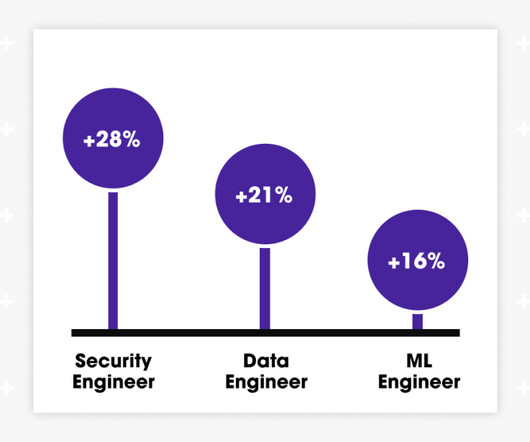
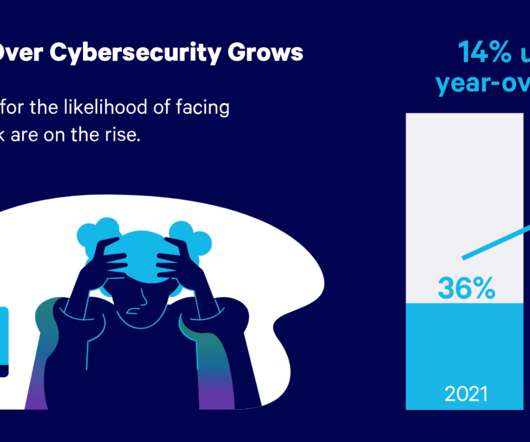
Cyberattacks continue to rise, increasing the need for robust data security. If you are partnering with a workplace equity software provider, you must be confident that your data is secure. Choose a vendor that adopts best practices in data security, supported by robust technology and certifications.


















































Let's personalize your content