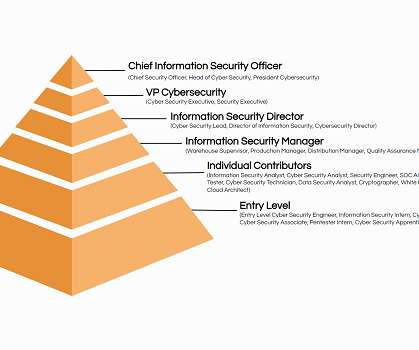
Top 30 Cyber Security Job Titles [+ Descriptions]
Ongig
JUNE 18, 2020
What are the best Cyber Security job titles for you and your team? I reviewed 150 Cyber Security titles searched for by candidates (and employers!) In this article, you’ll find: Cyber Security vs. Cybersecurity — Should it be 2 words or one? Cyber Security vs Cybersecurity?



























Let's personalize your content