How to Choose the Right Cyber Security Recruiter in California?
Recruiters Lineup
SEPTEMBER 17, 2024
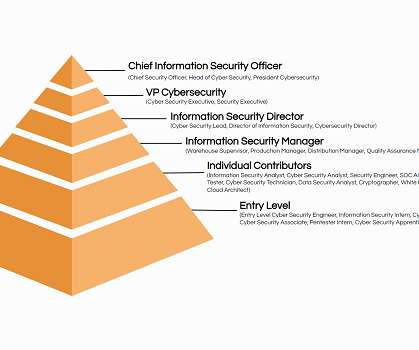
California is a tech-driven state, making it a prime target for increasingly sophisticated cyber threats. In this environment, hiring top cyber security talent is essential for businesses looking to protect their data and maintain security resilience. Why Hiring a Specialized Cyber Security Recruiter Is Crucial?












































Let's personalize your content