Top 10 Globally Recognized Certifications for Cyber Security
U-Next
SEPTEMBER 27, 2022
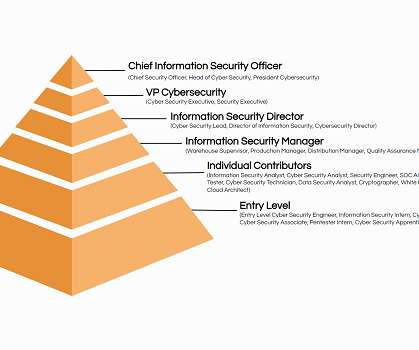
Certifications for cyber security are hence the gateway towards pursuing this booming and unique professional space. . While seeking a cyber security certification, the following can prove to be the best available choices for candidates as they have industry-recognized credentials and reputations.















































Let's personalize your content