Evaluating the Value of Cyber Awareness Training
PSB
JANUARY 25, 2025
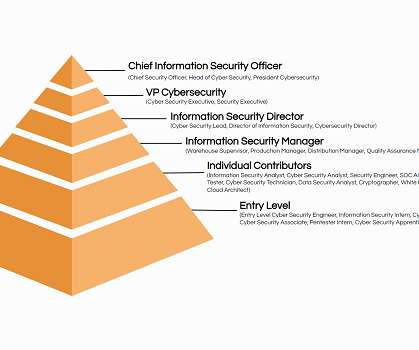
In todays rapidly evolving digital landscape, cyber threats are becoming more sophisticated, frequent, and costly. For organizations of all sizes, cybersecurity breaches can result in financial losses, reputational damage, and compliance penalties. This is where Cyber Security Awareness Training comes in.


















































Let's personalize your content