Staying safe from the latest HR and payroll scams in 2025
Cezanne
JULY 15, 2025
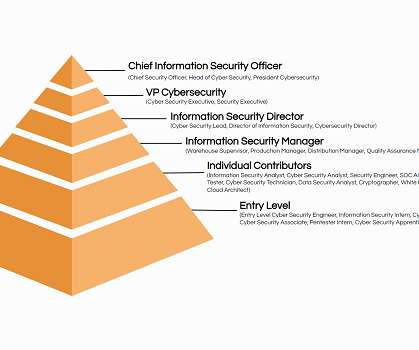
Practical steps like staff training, secure data sharing, and verification protocols are essential to prevent scams and protect both employee information and company funds. The UK’s National Cyber Security Centre has a wealth of free online resources worth checking out.2 Use a secure HR system (like Cezanne!)

















































Let's personalize your content