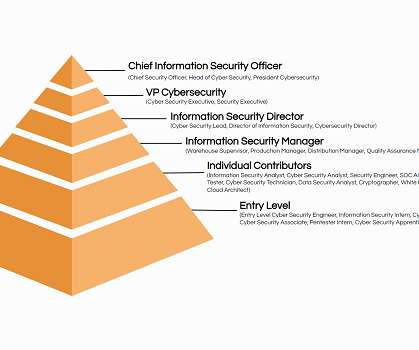
Cybersecurity policy essential components
Business Management Daily
FEBRUARY 18, 2025
Be clear about who is expected to set up any computer or mobile device IT security measures. In-office systems, the onsite IT department often plays a more significant role in updating security software programs on desktops. You should also remind them to update their antivirus software.




















































Let's personalize your content