How to Choose the Best Automotive Recruiter in Miami for Your Dealership
Recruiters Lineup
JULY 4, 2024
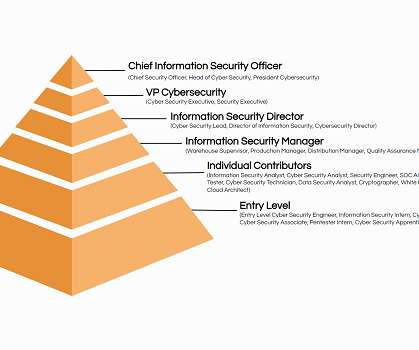
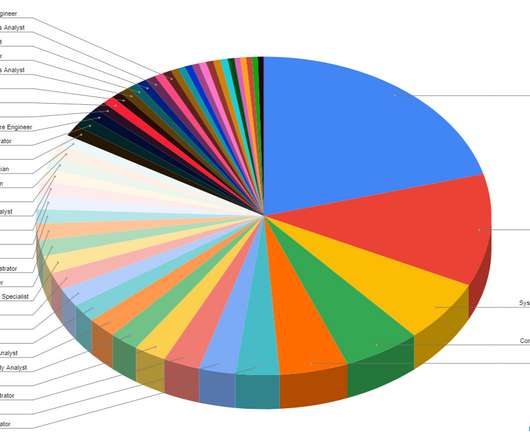
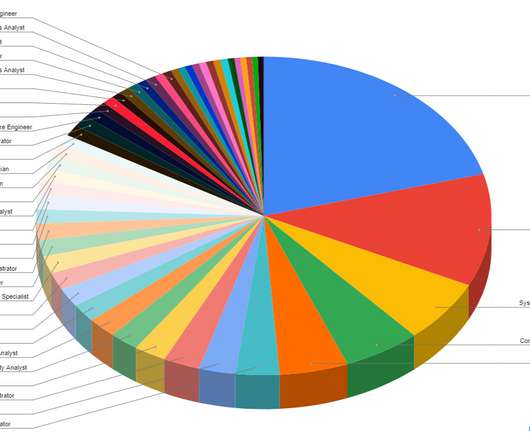
Automotive professionals face challenges like technical skills shortages, technological changes, talent competition, and diversity/inclusion initiatives. Dealership has adopted AI-driven technology, advanced cyber security, and modular platforms.















































Let's personalize your content